
Contingency Plan or Current Reality — How to Meet Critical Needs for Secure Remote Access and Collaboration


Even before the current Covid-19 pandemic, IT professionals faced hurdles to supporting a growing number of remote and mobile workers. However, the crisis has pushed this need from disaster contingency planning to reality. Many organizations now find they must urgently enable secure and reliable network access to people who work away from headquarters or a branch office.
The distributed workforce: perception vs. reality
Despite all the hype around the growth of distributed and mobile workforces, until now the trend was not quite as big as advertised. According to an IDC study [1] completed just prior to the onset of the current crisis, most (69%) of employees worked from a centralized or branch office and another 16% worked at remote company locations. And in spite of data showing 62% of U.S. workers indicated that their organization offers some flexibility regarding remote work, only 15% of employees regularly traveled or worked from home.
There is no reliable data regarding the current numbers because the situation is evolving so rapidly. Nonetheless, with approximately half the globe’s population under some form of stay-at-home order, it’s not hard to extrapolate to a huge percentage. And while there are optimistic estimates that the pandemic can be controlled within months—or at least in less than two years—surely things will not return to the old “normal” overnight.
This situation leaves the teams responsible for the corporate network and security – IT professionals like you – with a huge task. You need to provide network access and collaboration capabilities to an unprecedented number of people working remotely. At the same time, you need to make sure the network functions reliably with minimal latency and provides access to critical data and systems as securely as possible.
Remote access and collaboration is the new normal
Even post the current crisis, it is unlikely that this need for secure remote access will abate. Workers and companies will have discovered the efficiencies of web meetings, video conferences and standardized remote file sharing, which include huge benefits such as reduced travel costs and nimble collaboration. So, for today and in the future, you will need to ensure fast and seamless access to virtually all internal company resources.
In addition, third parties need secure access to internal data, machines and resources such as for providing remote tech support to users and machines. But it’s critical that you can control this access granularly to ensure these third parties only get access to the resources that they really need.
It’s not only about enabling connectivity, but you will also need to protect remote users from internet threats while browsing or using online meetings on remote machines and mobile devices. From lone wolf hackers to organized crime rings to nation states, bad actors are using increasingly sophisticated tools and malware to attack devices, networks, and backend systems. The current crisis is also opening new threat vectors. For example, Interpol has recently warned [2] that hackers are targeting hospitals responding to Covid-19 outbreak, remote workers using videoconferencing, and others. “With a huge number of people teleworking from home, often with outdated security systems, cyber-criminals prey on the opportunity to take advantage of this surreal situation and focus even more on cyber-criminal activities,” wrote Europol executive director Catherine De Bolle.
Old-school network infrastructure presents a huge hurdle
These needs to provide secure access with minimal latency will test your team’s readiness to support this massive offsite workforce. However, the reality on the ground may be that your network is not prepared. The same IDC study [1] found the network infrastructure supporting remote workers was not up to the task as compared to the network resources supporting office workers. Over 50% of respondents to the survey told IDC that they had difficulty communicating with and/or collaborating with internal colleagues, and 43% said that this difficulty extended to external customers and stakeholders. But even more striking, almost 40% said that they lacked effective remote access.
Control access to your internal infrastructure and protect traveling users
As a pioneer in converging the network with cloud-enabled security, Open Systems offers solutions to all of these challenges. This expertise includes everything from secure WAN access for remote users and third-party providers to seamlessly protected internet access for travelling users. We call this complete solution Secure Mobile Entry Point, and it supports an organization’s mobile workforce and partners by providing secure access to corporate network resources. Among the key benefits, it lets you:
- Control access to your internal infrastructure while protecting employees working from home
- Grant secure WAN and internet access to remote users
- Enable third parties to securely collaborate with internal users or remotely perform maintenance on their machines or on IoT devices
The basic concept underlying the unique effectiveness of Open Systems’ Mobile Entry Point is a seamless connection to the closest entry point. It establishes a network-level connection, allowing clients such as personal computers, laptops, and mobile phones to access network resources from home or from anywhere in the world as if they were on site. Clients are authenticated according to the organization’s policy, and access to corporate resources is granted based on the user’s privileges.
The Mobile Entry Point solution supports flexible deployment modes (cloud, on-premises) which allow for best global coverage. In addition, various authentication mechanisms are provided: password, user or machine certificates, SAML with Azure AD or other Cloud Identity Providers and optionally with a software/hardware token as a second factor. In the case of certificate-only authentication, a seamless connection to the Mobile Entry Point can be established without any action required from the user side.
It also provides secure access through built-in Secure Web Gateway and firewall functionalities. When connected to the closest Mobile Entry Point, this approach guarantees secure access to internal resources or external websites: Built-in firewall functionality allows you to assign different policies to different user groups, enabling you to granularly control access to corporate resources. Plus, Mobile Entry Point in combination with a built-in Secure Web Gateway provides secure internet access for mobile users. This seamless approach protects remote and mobile users with the same policy as when browsing from the corporate office.
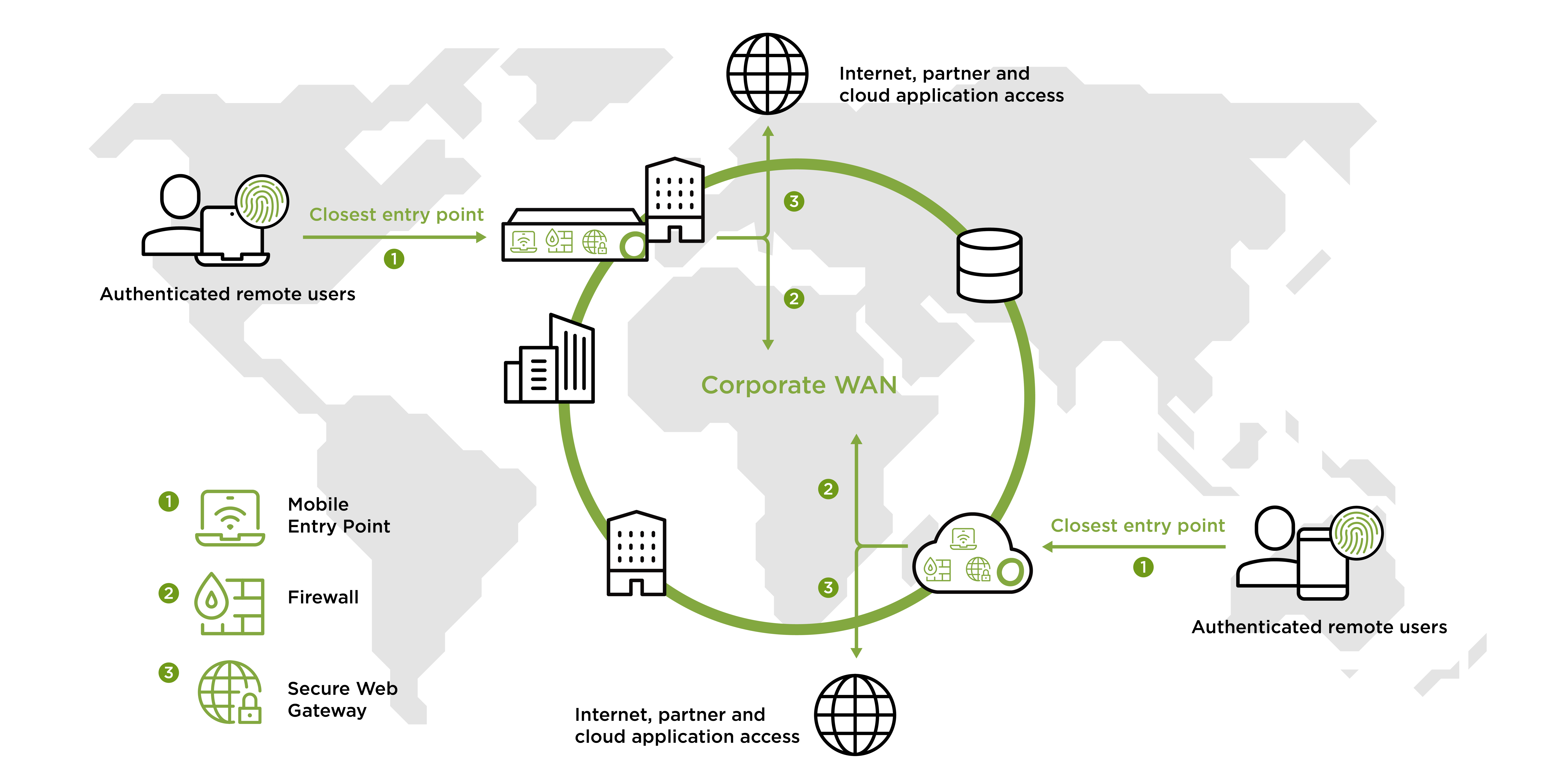
Mobile Entry Point provides global coverage through deployments either on premises or in the cloud (Azure, AWS). Remote users automatically connect to the closest Mobile Entry Point where built-in firewall and Secure Web Gateway functionalities guarantee secure access to internal resources or external websites.
All of this makes it possible to easily accommodate the unprecedented spike in remote and mobile users that IT teams have recently needed to support. Plus, with the Open Systems service, these teams don’t have to worry about time-consuming operational tasks. We cover the entire service chain – from robust architecture design to deployment and setup to 24x7 expert-level support through the whole software life cycle.
To find out more about how Open Systems can be your trusted partner for disaster and contingency plan support such as the current Covid-19 crisis visit https://www.open-systems.com/our-response-to-covid-19
[1] https://blogs.idc.com/2020/03/16/remote-work-in-the-covid-19-era-are-we-ready/
[2] https://www.europol.europa.eu/staying-safe-during-covid-19-what-you-need-to-know
Leave Complexity
Behind
To learn how Open Systems SASE Experience can benefit your organization, talk to a specialist today.
Contact Us


