
Mobile Entry Point
Enable Secure Remote Access for Mobile Users or Third Parties
Users work anytime and anywhere these days. They need to seamlessly and securely access all internal resources independent of where they are.
Enforcing security policies is especially important for mobile users. In addition, users should be protected from internet threats when browsing on their corporate devices, even if they are traveling and are out of the office.
Provide Secure Remote Access for
Your Mobile Users
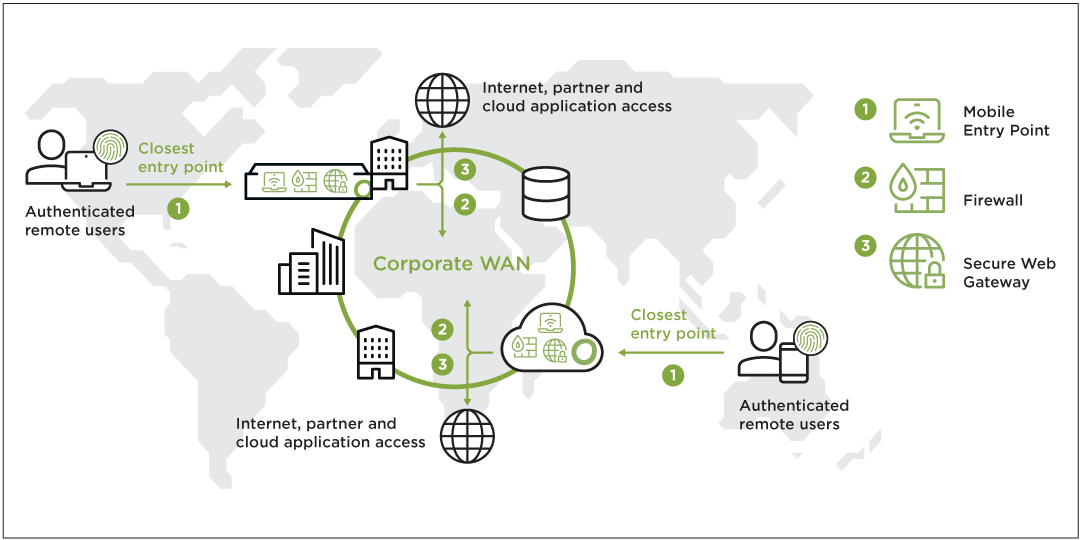
The Mobile Entry Point service provides secure remote access for mobile users. Connected users can access corporate resources using an encrypted and easy-to-establish connection.
Global Coverage
By deploying Mobile Entry Points (Access Points) to existing or additional SD-WAN edge devices, global coverage can be provided for your mobile users.
Due to the deployment on SD-WAN edge devices, a reliable and secure connection to the corporate WAN is available.
Secure Access
Strong cipher suites and regular patching provide a secure connection from the remote users to the corporate WAN.
Enforce security policies on endpoints by activating “always-on” to block all network traffic on endpoints if they are not connected to a Mobile Entry Point.
Expert-level Operations
Enjoy the peace of mind of 24×7 monitoring, incident handling, and change management – provided by our L3 engineers.
Central policy setup and control allows you to enforce global security policies and configuration.
By deploying Mobile Entry Points (Access Points) to existing or additional SD-WAN edge devices, global coverage can be provided for your mobile users.
Due to the deployment on SD-WAN edge devices, a reliable and secure connection to the corporate WAN is available.
Strong cipher suites and regular patching provide a secure connection from the remote users to the corporate WAN.
Enforce security policies on endpoints by activating “always-on” to block all network traffic on endpoints if they are not connected to a Mobile Entry Point.
Enjoy the peace of mind of 24×7 monitoring, incident handling, and change management – provided by our L3 engineers.
Central policy setup and control allows you to enforce global security policies and configuration.
How Does the Mobile Entry Point Solution Work?
Access Point Selection
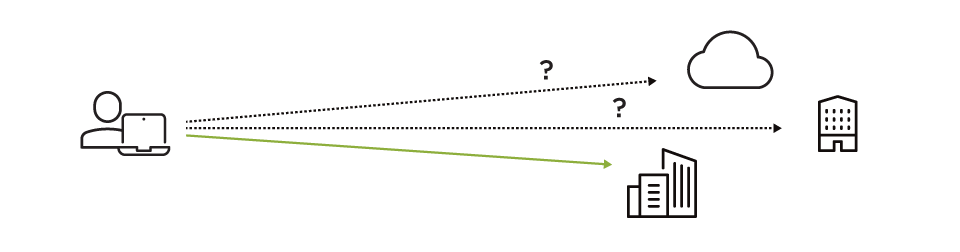
Either fixed, manually selectable or using a GeoDNS provider of choice, the right Mobile Entry Point is selected (on-premises or in the cloud).
Authentication
Depending on a customer’s requirement, authentication can either be done using username/password or a combination of user credentials and software/hardware tokens. Using certificates further improves the security or even allows seamless user authentication by using the certificate only.
Secure Connection
A secure and encrypted (DTLS) connection is established between the client and the Mobile Entry Point so that the exchanged traffic is encrypted and remains private.
Routing Optimizations
Define routing policies for trusted applications to use the local internet breakout of the remote user or to allow access to the local LAN.
Either fixed, manually selectable or using a GeoDNS provider of choice, the right Mobile Entry Point is selected (on-premises or in the cloud).

Depending on a customer’s requirement, authentication can either be done using username/password or a combination of user credentials and software/hardware tokens. Using certificates further improves the security or even allows seamless user authentication by using the certificate only.

A secure and encrypted (DTLS) connection is established between the client and the Mobile Entry Point so that the exchanged traffic is encrypted and remains private.

Define routing policies for trusted applications to use the local internet breakout of the remote user or to allow access to the local LAN.
Leave Complexity
Behind
To learn how Open Systems SASE Experience can benefit your organization, talk to a specialist today.
Contact Us



